At this stage, we have all (or most) of our Tier0 objects ready; and most (if not all) delegations are in place representing all roles defined i our Delegation Model. Now is time to configure our Admin Area (Tier0). All those configurations are to maintain Tier0 integrity over time, while having a central configuration. This will make our infrastructure more manageable and secure over the coming years.
- Create & Configure GPOs
- Import GPO templates
- Set GPO Restrictions
Create & Configure GPOs
After over 2 decades of having GPOs, we still having many diverse strategies on how many GPOs do we need. This have raised the number of GPOs too much; the lack of a strong strategy.
As the definition says: a GPO is a set of configurations which can be centrally applied. Applied to whom? Simple, just to Users and/or computers. So here we define the first rule:
Any GPO created must be defined to be either for Users or for Computers, but not for both.
A very common bad practice is that every time a new setting is need, a new GPO is created. In order to avoid these bad practices, we have to define how are we going to manage these GPOs, and when is “valid” to create a new one. Create the GPOs as Monolithic GPO. Meaning of this is that 90% or 95% of the configurations will be done using the same GPO object, and only the remaining configurations which are not compatible with the monolithic GPO will be configured on another GPO. New GPO will ONLY be created when the existing (monolithic) GPO is not compatible with the new setting.
- Monolithic GPO refers to a consolidated GPO which will have ALL settings configured.
- Monolithic GPO will be either COMPUTER or USER, but not both.
- Monolithic GPO strategy is to have the fewest number of GPO within the hierarchy:
- 2 GPOs at domain level (1 user and 1 computer | GENERAL)
- 2 GPOs at sites (1 user and 1 computer | GLOBAL)
- 3 GPOs at site level (1 user, 1 Desktop and 1 Laptop)
- Exceptions might exist, previous analysis and authorization by corresponding AD Architect board.
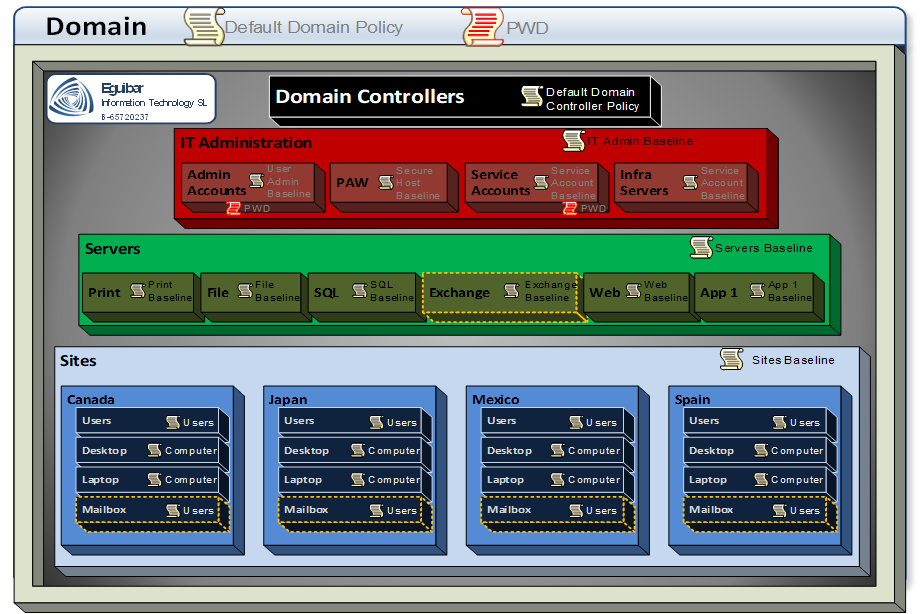
For more information please read more on “Monolithic GPO”.
After reviewing our GPO strategy, and most important, the “monolithic GPO” concept, we can start creating all required GPOs for Configuring Admin Area (Tier0). The New-DelegateAdGpo wrapper function will check for existence of a GPO, creating it in case it does not exists; it will grant the previously defined GPO Admin Rights group to edit, modify, delete & security; disable the corresponding section of the GPO (If user settings, disable computer & viceversa); link the GPO to its corresponding Ldap path; and in case a backup template needs to be imported, the process it accordingly.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 |
# Create Baseline GPO Write-Verbose -Message 'Creating Baseline GPOs and configure them accordingly...' # Domain $parameters = @{ gpoDescription = 'Baseline' gpoLinkPath = $AdDn GpoAdmin = $sl_GpoAdminRight.SamAccountName gpoBackupPath = Join-Path $DMscripts SecTmpl } New-DelegateAdGpo @parameters -gpoScope 'C' -gpoBackupID $confXML.n.Admin.GPOs.PCbaseline.backupID New-DelegateAdGpo @parameters -gpoScope 'U' -gpoBackupID $confXML.n.Admin.GPOs.Userbaseline.backupID # Domain Controllers $parameters = @{ gpoDescription = '{0}-Baseline' -f $confXML.n.Admin.GPOs.DCBaseline.Name gpoScope = $confXML.n.Admin.GPOs.DCBaseline.Scope gpoLinkPath = 'OU=Domain Controllers,{0}' -f $AdDn GpoAdmin = $sl_GpoAdminRight.SamAccountName gpoBackupId = $confXML.n.Admin.GPOs.DCBaseline.backupID gpoBackupPath = Join-Path $DMscripts SecTmpl } New-DelegateAdGpo @parameters # Admin Area New-DelegateAdGpo -gpoDescription 'ItAdmin-Baseline' -gpoScope 'C' -gpoLinkPath $ItAdminOuDn -GpoAdmin $sl_GpoAdminRight.SamAccountName New-DelegateAdGpo -gpoDescription 'ItAdmin-Baseline' -gpoScope 'U' -gpoLinkPath $ItAdminOuDn -GpoAdmin $sl_GpoAdminRight.SamAccountName New-DelegateAdGpo -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItAdminOU.Name) -gpoScope U -gpoLinkPath $ItAdminAccountsOuDn -GpoAdmin $sl_GpoAdminRight.SamAccountName -gpoBackupId $confXML.n.Admin.GPOs.AdminUserbaseline.backupID -gpoBackupPath (Join-Path $DMscripts SecTmpl) # Service Accounts $parameters = @{ gpoScope = 'U' GpoAdmin = $sl_GpoAdminRight.SamAccountName } New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItServiceAccountsOU.Name) -gpoLinkPath $ItServiceAccountsOuDn New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItSAT0OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItSAT0OU.Name, $ItServiceAccountsOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItSAT1OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItSAT1OU.Name, $ItServiceAccountsOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItSAT2OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItSAT2OU.Name, $ItServiceAccountsOuDn) # PAWs $parameters = @{ gpoScope = 'C' GpoAdmin = $sl_GpoAdminRight.SamAccountName } New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawOU.Name) -gpoLinkPath $ItPawOuDn -gpoBackupId $confXML.n.Admin.GPOs.PAWbaseline.backupID -gpoBackupPath (Join-Path $DMscripts SecTmpl) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT0OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItPawT0OU.Name, $ItPawOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT1OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItPawT1OU.Name, $ItPawOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT2OU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItPawT2OU.Name, $ItPawOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawStagingOU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItPawStagingOU.Name, $ItPawOuDn) # Infrastructure Servers $parameters = @{ gpoScope = 'C' GpoAdmin = $sl_GpoAdminRight.SamAccountName } New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraOU.Name) -gpoLinkPath $ItInfraOuDn -gpoBackupId $confXML.n.Admin.GPOs.INFRAbaseline.backupID -gpoBackupPath (Join-Path $DMscripts SecTmpl) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT0.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItInfraT0.Name, $ItInfraOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT1.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItInfraT1.Name, $ItInfraOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT2.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItInfraT2.Name, $ItInfraOuDn) New-DelegateAdGpo @parameters -gpoDescription ('{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraStagingOU.Name) -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItInfraStagingOU.Name, $ItInfraOuDn) # redirected containers (X-Computers & X-Users) New-DelegateAdGpo -gpoDescription ('{0}-LOCKDOWN' -f $confXML.n.Admin.OUs.ItNewComputersOU.Name) -gpoScope C -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItNewComputersOU.Name, $AdDn) -GpoAdmin $sl_GpoAdminRight.SamAccountName New-DelegateAdGpo -gpoDescription ('{0}-LOCKDOWN' -f $confXML.n.Admin.OUs.ItNewUsersOU.Name) -gpoScope U -gpoLinkPath ('OU={0},{1}' -f $confXML.n.Admin.OUs.ItNewUsersOU.Name, $AdDn) -GpoAdmin $sl_GpoAdminRight.SamAccountName # Housekeeping New-DelegateAdGpo -gpoDescription ('{0}-LOCKDOWN' -f $confXML.n.Admin.OUs.ItHousekeepingOU.Name) -gpoScope U -gpoLinkPath $ItHousekeepingOuDn -GpoAdmin $sl_GpoAdminRight.SamAccountName New-DelegateAdGpo -gpoDescription ('{0}-LOCKDOWN' -f $confXML.n.Admin.OUs.ItHousekeepingOU.Name) -gpoScope C -gpoLinkPath $ItHousekeepingOuDn -GpoAdmin $sl_GpoAdminRight.SamAccountName |
Import GPO templates
The wrapper function New-DelegateAdGpo can restore the GPO during creation time, but this can also be accomplished in case GPO already exist. Remember that when importing a GPO, all previous existing settings will get removed, and only the settings from the backup will remain. Those mentioned backup templates can be found on several places, like Microsoft Security Compliance Toolkit, Microsoft Security Baselines Blog or Center for Internet Security (CIS)
This is exactly the case for already existing “Default Domain” & “Default Domain Controllers” GPOs.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
# Import Default Domain policy backup $splat = @{ BackupId = $confXML.n.Admin.GPOs.DefaultDomain.backupID TargetName = $confXML.n.Admin.GPOs.DefaultDomain.Name path = (Join-Path -Path $DMscripts -ChildPath SecTmpl) } Import-GPO @splat # Import Default Domain COntroller policy backup $splat = @{ BackupId = $confXML.n.Admin.GPOs.DefaultDomainController.backupID TargetName = $confXML.n.Admin.GPOs.DefaultDomainController.Name path = (Join-Path -Path $DMscripts -ChildPath SecTmpl) } Import-GPO @splat |
Set GPO Restrictions
This section is the key for the Tier Model to be compliant. By setting up the Rights each tier has, we can ensure that Semi-Privileged and Privileged accounts are able to logon ONLY to the tier they belong to.
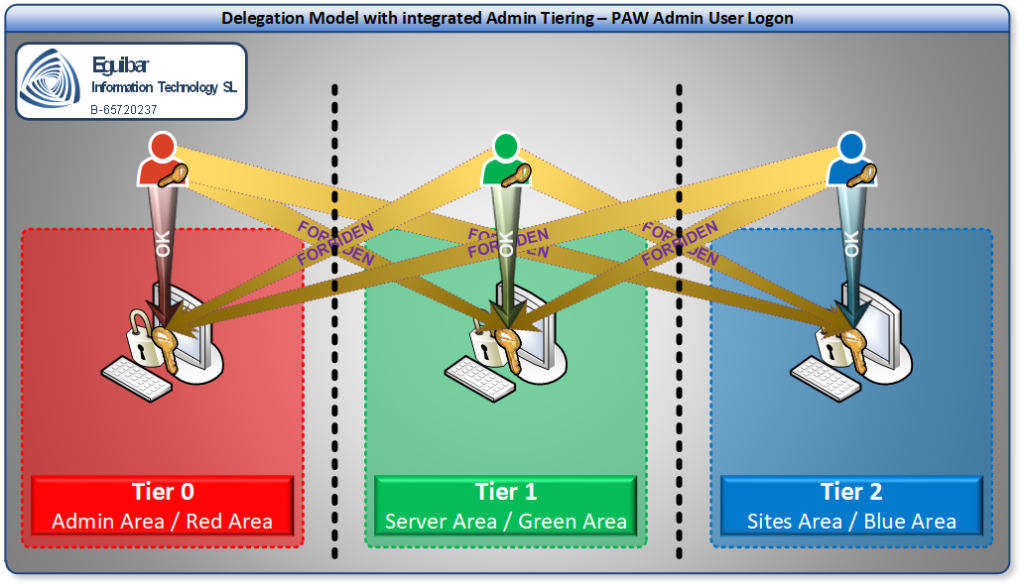
The Set-GpoPrivilegeRights will help us to implement such restrictions while Configuring Admin Area (Tier0), having the parameter to configure NetworkLogon, DenyNetworkLogon, InteractiveLogon, DenyInteractiveLogon, RemoteInteractiveLogon, DenyRemoteInteractiveLogon, BatchLogon, DenyBatchLogon, ServiceLogon and DenyServiceLogon.
Domain Restrictions
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
# Configure GPO Restrictions based on Tier Model # Domain $Splat = @( 'ALL SERVICES', 'ANONYMOUS LOGON', 'NT AUTHORITY\Local Account', 'NT AUTHORITY\Local Account and member of administrators group' ) Set-GpoPrivilegeRights -GpoToModify 'C-Baseline' -DenyNetworkLogon $Splat $parameters = @( $SG_Tier0ServiceAccount.SamAccountName, $SG_Tier1ServiceAccount.SamAccountName, $SG_Tier2ServiceAccount.SamAccountName ) Set-GpoPrivilegeRights -GpoToModify 'C-Baseline' -DenyInteractiveLogon $parameters $parameters = @( $SG_Tier0ServiceAccount.SamAccountName, $SG_Tier1ServiceAccount.SamAccountName, $SG_Tier2ServiceAccount.SamAccountName, $AdminName, $newAdminName ) Set-GpoPrivilegeRights -GpoToModify 'C-Baseline' -DenyRemoteInteractiveLogon $parameters $parameters = @( $SG_Tier0Admins.SamAccountName, $SG_Tier1Admins.SamAccountName, $SG_Tier2Admins.SamAccountName, 'Schema Admins', 'Enterprise Admins', 'Domain Admins', 'Administrators', 'Account Operators', 'Backup Operators', 'Print Operators', 'Server Operators', $AdminName, $newAdminName ) Set-GpoPrivilegeRights -GpoToModify 'C-Baseline' -DenyBatchLogon $parameters -DenyServiceLogon $parameters $parameters = @( 'Network Service', 'NT SERVICE\All Services' ) Set-GpoPrivilegeRights -GpoToModify 'C-Baseline' -ServiceLogon $parameters |
Domain Controllers Restrictions
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
# Configure GPO Restrictions based on Tier Model # Domain Controllers $parameters = @( $SG_Tier1ServiceAccount.SamAccountName, $SG_Tier2ServiceAccount.SamAccountName, $SG_Tier0Admins.SamAccountName, $SG_Tier1Admins.SamAccountName, $SG_Tier2Admins.SamAccountName, 'Schema Admins', 'Enterprise Admins', 'Domain Admins', 'Administrators', 'Account Operators', 'Backup Operators', 'Print Operators', 'Server Operators', $AdminName, $newAdminName ) Set-GpoPrivilegeRights -GpoToModify 'C-DomainControllers-Baseline' -DenyBatchLogon $parameters -DenyServiceLogon $parameters Set-GpoPrivilegeRights -GpoToModify 'C-DomainControllers-Baseline' -BatchLogon $SG_Tier0ServiceAccount.SamAccountName -ServiceLogon $SG_Tier0ServiceAccount.SamAccountName, 'Network Service' $parameters = @( $SG_Tier0Admins.SamAccountName, 'Schema Admins', 'Enterprise Admins', 'Domain Admins', 'Administrators', $AdminName, $newAdminName ) Set-GpoPrivilegeRights -GpoToModify 'C-DomainControllers-Baseline' -InteractiveLogon $parameters -RemoteInteractiveLogon $parameters $parameters = @( $SG_Tier1ServiceAccount.SamAccountName, $SG_Tier2ServiceAccount.SamAccountName, $SG_Tier1Admins.SamAccountName, $SG_Tier2Admins.SamAccountName, 'Account Operators', 'Backup Operators', 'Print Operators' ) Set-GpoPrivilegeRights -GpoToModify 'C-DomainControllers-Baseline' -DenyInteractiveLogon $parameters |
Admin Area Restrictions
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 |
# Admin Area $parameters = @( $SG_Tier1ServiceAccount.SamAccountName, $SG_Tier2ServiceAccount.SamAccountName, $SG_Tier0Admins.SamAccountName, $SG_Tier1Admins.SamAccountName, $SG_Tier2Admins.SamAccountName, 'Schema Admins', 'Enterprise Admins', 'Domain Admins', 'Administrators', 'Account Operators', 'Backup Operators', 'Print Operators', 'Server Operators', $AdminName, $newAdminName ) Set-GpoPrivilegeRights -GpoToModify 'C-ItAdmin-Baseline' -DenyBatchLogon $parameters -DenyServiceLogon $parameters $parameters = @( $SG_Tier0ServiceAccount.SamAccountName 'Network Service', 'NT SERVICE\All Services' ) Set-GpoPrivilegeRights -GpoToModify 'C-ItAdmin-Baseline' -BatchLogon $SG_Tier0ServiceAccount.SamAccountName -ServiceLogon $parameters # Admin Area = HOUSEKEEPING $parameters = @( $SG_Tier0Admins.SamAccountName, 'Domain Admins', 'Administrators' ) Set-GpoPrivilegeRights -GpoToModify 'C-Housekeeping-LOCKDOWN' -NetworkLogon $parameters -InteractiveLogon $parameters # Admin Area = Infrastructure Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT0.Name) -InteractiveLogon $SL_PISM.SamAccountName, 'Domain Admins', Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT0.Name) -RemoteInteractiveLogon $SL_PISM.SamAccountName $parameters = @( $SG_Tier0ServiceAccount.SamAccountName 'Network Service', 'NT SERVICE\All Services' ) Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT0.Name) -BatchLogon $SG_Tier0ServiceAccount.SamAccountName -ServiceLogon $parameters Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT1.Name) -InteractiveLogon $SG_Tier1Admins.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT1.Name) -RemoteInteractiveLogon $SG_Tier1Admins.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT1.Name) -BatchLogon $SG_Tier1ServiceAccount.SamAccountName -ServiceLogon $SG_Tier1ServiceAccount.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT2.Name) -InteractiveLogon $SG_Tier2Admins.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT1.Name) -RemoteInteractiveLogon $SG_Tier2Admins.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraT2.Name) -BatchLogon $SG_Tier2ServiceAccount.SamAccountName -ServiceLogon $SG_Tier2ServiceAccount.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraStagingOU.Name) -InteractiveLogon $SL_PISM.SamAccountName, 'Domain Admins', Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItInfraStagingOU.Name) -RemoteInteractiveLogon $SL_PISM.SamAccountName # Admin Area = PAWs Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawStagingOU.Name) -InteractiveLogon $SL_PAWM.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawStagingOU.Name) -RemoteInteractiveLogon $SL_PAWM.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT0OU.Name) -InteractiveLogon $SL_PAWM.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT0OU.Name) -RemoteInteractiveLogon $SL_PAWM.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT0OU.Name) -BatchLogon $SG_Tier0ServiceAccount.SamAccountName -ServiceLogon $SG_Tier0ServiceAccount.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT1OU.Name) -InteractiveLogon $SG_Tier1Admins.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT1OU.Name) -RemoteInteractiveLogon $SG_Tier1Admins.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT1OU.Name) -BatchLogon $SG_Tier1ServiceAccount.SamAccountName -ServiceLogon $SG_Tier1ServiceAccount.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT2OU.Name) -InteractiveLogon $SG_Tier2Admins.SamAccountName, Administrators Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT2OU.Name) -RemoteInteractiveLogon $SG_Tier2Admins.SamAccountName Set-GpoPrivilegeRights -GpoToModify ('C-{0}-Baseline' -f $confXML.n.Admin.OUs.ItPawT2OU.Name) -BatchLogon $SG_Tier2ServiceAccount.SamAccountName -ServiceLogon $SG_Tier2ServiceAccount.SamAccountName |